PROTECTING COMMUNITIES
A PEOPLE-CENTRIC APPROACH TO MANAGING
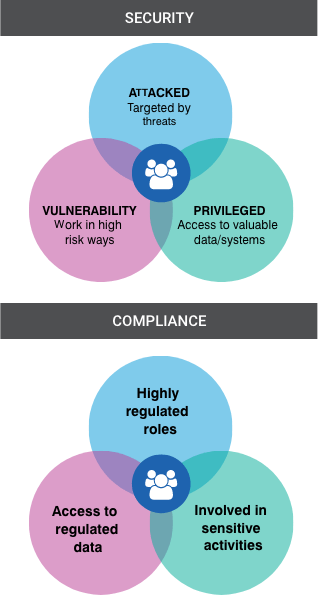
VULNERABILITY, ATTACKS AND PRIVILEGE
1. PROTECTING COMMUNITIES:
A PEOPLE-CENTRIC APPROACH TO MANAGING VULNERABILITY, ATTACKS AND PRIVILEGE
Organizations are spending more than ever on cybersecurity and getting less value from it. Attacks keep getting through.
2. TODAY’S ATTACKS TARGET PEOPLE, NOT INFRASTRUCTURE.
It’s time for a fundamental rethink. Traditional cybersecurity models were built for an earlier era— when the prevailing security model was to lock down the perimeter and deal with threats after they got though
3. WHY PROTECTION STARTS WITH PEOPLE
It’s clear that the usual defend-the-perimeter model of cybersecurity isn’t working—and hasn’t worked for years.
TODAY’S ATTACKS TARGET PEOPLE, NOT
INFRASTRUCTURE.
Organizations are spending more than ever on cybersecurity and getting less value from it. Attacks keep getting through. Sensitive information keeps falling into the wrong hands. And data breaches keep making headlines.
It’s time for a fundamental rethink. Traditional cybersecurity models were built for an earlier era—when the prevailing security model was to lock down the perimeter and deal with threats after they got though. The approach barely worked then; it’s hopelessly broken now.
That’s because people, not technology, are attackers’ biggest target—and your biggest risk. This change in the threat landscape requires a fresh mindset and new strategy, one that focuses on protecting people rather than the old perimeter.
But what does this new approach look like in practice? This guide explores that question by outlining the foundational elements of security in the modern era.
It describes the factors that play into end-user risk. It explains how to mitigate these factors. And it recommends concrete steps you can take to build a people-centric defense.
WHY PROTECTION STARTS WITH PEOPLE
It’s clear that the usual defend-the-perimeter model of cybersecurity isn’t working—and hasn’t worked for years. More than two thirds of IT security professionals polled in a recent Ponemon study expect cyber attacks to “seriously diminish their organization’s shareholder value.” And more than believe their cybersecurity posture is leveling off or even declining.
Blame two converging trends: the perimeter is dissolving, and attackers are shifting their focus away from technology and towards people.
And the walls came tumbling down
There’s a simple reason perimeter defenses aren’t working. In today’s cloud-enabled mobile economy, there’s no longer a perimeter to defend. Work takes place on devices organizations don’t support, on infrastructure they don’t manage, and in channels they don’t own.
As Gartner puts it, the IT department “simply does not control the bounds of an organization’s information and technology in the way it used to.”
People always make the best exploits
As business shifts to the cloud, so have attackers. Cloud infrastructure may be highly secure, but the people who use them are often vulnerable.
That’s why today’s attacks exploit human nature rather than technical vulnerabilities. More than 99% of today’s cyber attacks are human-activated. These attacks rely on a person at the other end to open a weaponized document, click on an unsafe link, type their credentials, or even carry out the attacker’s commands directly (such as wiring money or sending sensitive files).
Credential phishing, which tricks users into entering their account credentials into a fake login form, is one of the most dangerous examples. In the cloud era, those credentials are the keys to everything—email, sensitive data, private appointments and trusted relationships.
In the third quarter of 2018, for example, corporate credential phishing attempts quadrupled vs. the year-ago quarter. And email fraud rose 77% over the same timeframe.
