Reprinted by permission from Gartner - Licensed for Distribution
Phishing attacks are increasingly using impersonation to bypass traditional defense mechanisms. Weak sender identification will continue to present opportunities for creative attacks. Security and risk management leaders should use this research to adjust their strategy and business processes.
Overview
Key Challenges
- Phishing attacks are still increasing as a targeting method of attackers. Phishing attacks targeting credentials will continue to escalate as applications and data migrate to better-protected cloud providers.
- Email is not designed to truly authenticate sender identity. Efforts like DMARC to authenticate domains are not granular enough to authenticate users and do not address all attack types.
- Most implemented secure email gateways (SEGs) are not designed with post-delivery detection and remediation techniques, costing incident responder and email admin time and reducing the feedback loop from end users.
- User phishing education is a good start toward people-centric security, but current email security does not provide users with any indicators of the trust they can put in emails or the proper workflow for dealing with suspect emails.
Recommendations
Security and risk management leaders responsible for endpoint and mobile security should:
- Upgrade secure email gateway solutions to cloud versions that include phishing protection, particularly for impostor or business email compromise (BEC) protection.
- Integrate employees into the solution and build capabilities to detect and respond to suspected attacks.
- Work with business managers to develop standard operating procedures for handling sensitive data and financial transactions.
Strategic Planning Assumptions
By 2023, sender identity verification will be a common critical component on secure email gateways and other anti-phishing solutions.
By 2023, anti-phishing education will be a critical part of the feedback loop between end users and email security solutions.
Through 2023, business compromise attacks will be persistent and evasive, leading to large financial fraud losses for enterprises and data breaches for healthcare and government organizations.
Introduction
Phishing in its various forms is increasing1 and will continue to increase through the planning time horizon. Most secure email gateway vendors are not responding fast enough to increasing phishing attacks.
Security and risk managers (SRMs) should take a three-pronged approach to improve their defenses against phishing attacks:
Upgrade secure email gateway and other controls to improve protection for phishing.
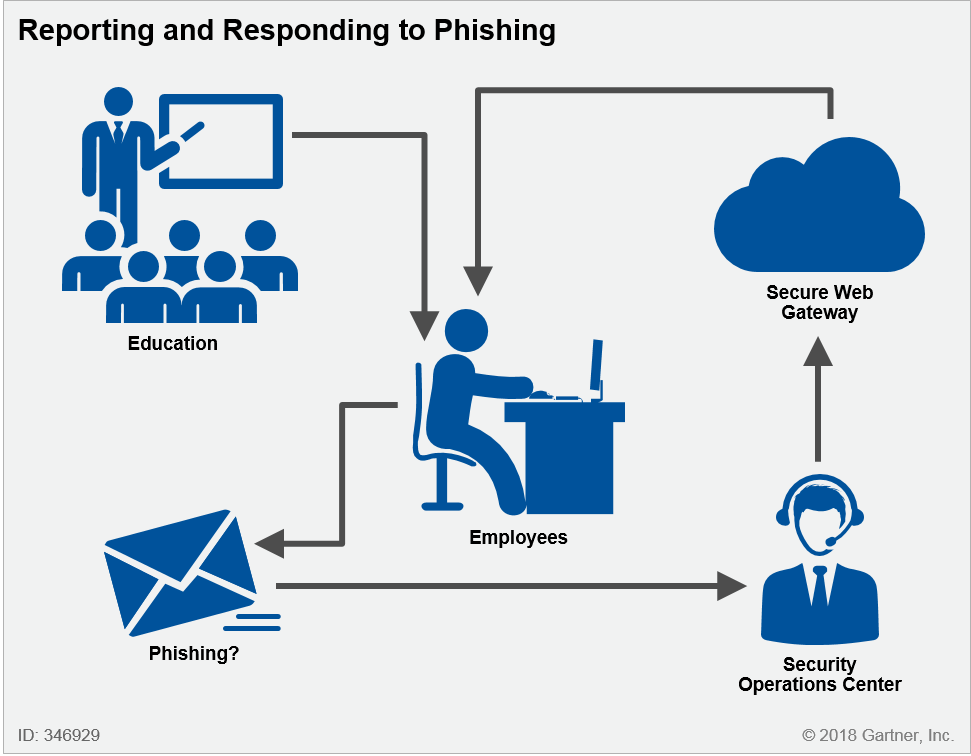
Integrate employees into the solution and build capabilities to detect and respond to suspect attacks (see Figure 1).
Work with business managers to develop standard operating procedures for handling sensitive data and financial transactions.
Figure 1. Integrate Employees Into the Solution
Analysis
Upgrade Secure Email Gateway and Other Controls to Improve Protection Against Phishing
The current wave of phishing attacks caught many anti-spam solution providers by surprise, and most are now struggling to catch up with rapidly changing attack trends.
Phishing attacks come in three general forms:
- Impersonation or BEC attacks (see Note 1)
- Malicious attachments
- Malicious web links
Impersonation or Business Email Compromise Attack Protection
Of these three, impersonation attacks are the most difficult to detect and most critical to be solved in the secure email gateway. Malicious attachments and web link phishing attacks are mitigated by endpoint protection solutions that block malware execution and secure web gateways (SWGs) that filter web content. However, there is no technological second security layer for impersonation attacks. Email is not designed to truly authenticate sender identity. Efforts like DMARC to authenticate domains are not granular enough to authenticate users and do not address spoofing, cousin or look-alike domain usage (see Note 2) or disposable consumer email accounts like Gmail. Moreover, these attacks are harder to detect because they have fewer indicators of malicious intent. State-of-the-art protection for impersonation attacks involves machine learning to detect anomalies in an email from senders that are a near match with previous communication partners and keyword analysis. While machine learning is promising, it will increase potential false positives that must be addressed by the security operations center (SOC) or employees, and a process must be established to address false positives/negatives.
Phishing protection is generally aimed at impersonation attacks where the phisher is using another email account to imitate someone the recipient has a relationship with. More troubling, however, is that phishing attackers are also infiltrating email systems with account takeover attacks and exploiting access to phish business partners using legitimate email accounts. Because these are legitimate accounts, this is a much harder problem to solve. Multifactor authentication (MFA) and user and entity behavioral analytics solutions are good controls to detect employee account takeover, but they cannot detect a takeover attack with a business partner.
Impersonation attacks will continue to increase and cause continuous problems over the five-year planning horizon. In addition to SEG-based solutions, some organizations use digital certificates in Outlook. However, currently, Outlook digital certificates are clunky and unfriendly ways to identity proof senders and are difficult to manage. Email encryption cannot provide identity proofing of new communication partners, but it can authenticate users during an ongoing relationship or transaction. Encryption solutions are often reported as difficult and unfriendly to use especially on mobile devices. Google recently launched "Confidential" mode that enables users to create emails protected by lite digital rights management capability in the Gmail interface. Microsoft O365 encryption uses the Microsoft account identity, which achieves the same end. Certificates and encryption provide the untapped opportunity for preventing imposters from injecting themselves into transactional email threads, but they must be embedded into the email interface and easy-to-use for senders and recipients.
Malicious Attachment Protection
Malicious attachments are detected in advanced solutions using a gauntlet of signatures, static analysis, and dynamic sandboxing analysis. However, malware is increasingly sandbox-aware2 and obfuscated such that these layers must constantly evolve to remain effective. Email policy should block all nonstandard file types. More drastic measures to thwart attachments are to strip all active code from attachments and deliver only the disarmed versions. This is commonly called content disarm and reconstruction (CDR). However, the security value of CDR needs to be balanced with the business need for macro- or JavaScript-enabled content. Still, CDR should be considered a best practice for general populations with exceptions granted for specific roles or users. Group policy to prevent automatic execution of macros is also a best practice prevention; however, malware authors are adept at convincing users to enable macros and not all attacks use macros. Indeed, recent attacks have used hidden file share request to capture user account hashes. SRM leaders should also consider behavioral endpoint protection solutions that can catch malicious files and actions on the endpoint as part of an effective anti-phishing strategy (see "Redefining Endpoint Protection for 2017 and 2018"). Additionally, some endpoint solutions (e.g., Bromium and Comodo Cybersecurity) are starting to only open documents from email clients in isolated containers where they can be viewed and interacted with, but they cannot change the state of the PC (see "Magic Quadrant for Endpoint Protection Platforms").
Malicious Web Link Protection
Using best practices for preventing malicious URL links involves a two-step process:
The vendor first detects and removes any known bad URLs, then attempts to validate or verify the destination of unknown or "safe" URLs, discarding those that resolve to malicious sites or suspicious content.
Any remaining hyperlinks in the email are replaced with newly encoded hyperlinks that act as a proxy via the anti-phishing provider, allowing a click-time URL reputation and website check.
The added advantage of this system is that user clicks are recorded in case the reputation changes, and it provides data for the detection and response activities. Phishing education needs to account for URL rewriting, as it should not be treated as giving license to click on anything. SWGs are an effective secondary security layer for link-based attacks, but only if they cover all endpoints in and out of the network (see "Magic Quadrant for Secure Web Gateways"). Endpoint solutions are also an effective layer against web-based attacks. Browser isolation — either in the SEG (e.g., Proofpoint, Symantec), on the endpoint (e.g., Bromium) or in an SWG (e.g., Menlo Security, Symantec) — is another tool to effectively isolate the endpoint from the effects of active code on malicious websites. However, isolation needs to be configured to read only to prevent account takeover attacks that exploit fake log-in pages.
As more data and transactions move to the cloud, account takeover attacks will increase. Phishing is an effective method to direct users to web log-on pages that impersonate legitimate cloud applications. Future SEG solutions must be effective at detecting and blocking URLs of faked popular web log-on pages. MFA for all cloud applications is a good second layer of protection.
Upgrade Existing Secure Email Gateways to Include Phishing Specifically
Most anti-spam solutions do not fully address phishing attacks, and most solution providers have add-on solutions to address phishing. Email boxes are migrating to the cloud, mostly Exchange Online (Office 365), enabling new architectures, specifically cloud prefilters or mailbox API post-delivery-based solutions. Cloud solutions are better-positioned to be agile and adapt to new threats without requiring admins to upgrade on-premises software or appliances. New solutions (see "How to Build an Effective Email Security Architecture") should also consider internal email traffic filtering to address account takeover attacks. Microsoft has an opportunity and an incentive to solve the phishing issues, but based on historical results, it must become more agile and respond more rapidly to changing attacker tactics. As Microsoft's SEG market share increases, smart attackers will specifically target Microsoft's defenses. Vendors that have been fully focused on this market are responding more rapidly to changing threats than vendors that offer broad portfolios of security services.
To date, most solution providers have assumed filtering is catching and will continue to catch, all phishing messages. This is a dangerous assumption. History has shown that effective email filtering techniques result in attackers responding with new innovative attacks. Solution providers need to adopt a more adaptive security architecture approach (ASA; see "Designing an Adaptive Security Architecture for Protection From Advanced Attacks"). ASA assumes that protection will be less than perfect and builds in detection and response capabilities to rapidly detect missed messages, investigate, and remediate by "clawing back" messages that were missed from inboxes. Users can provide an effective post-delivery detection capability if they are properly equipped (see below). Other detection techniques involve integration with endpoint and web filtering tools and continuous threat intelligence feeds. Clawback capabilities are also critical for responding to threats. Clawback should allow users to search for specific emails already delivered and remove ("clawback") malicious emails from inboxes.
Advanced reporting is also an often missing component in many SEG solutions. Mature security organizations that are under constant attack require better reporting on who is being targeted and by whom, so they can better harden their business process and technical controls. All organizations would benefit from better statistics on the level of phishing in their organization versus the overall level of phishing in market/industry/groups. False positive and false negative reporting is also critical for IT groups to measure their effectiveness trends and to provide reporting to business management. When solutions provide users with the tools to report phishing and spam, confirmed reports can be used to calculate false negative rates. Similarly, releasing emails from quarantines can provide a proxy for false positive results. Pressure vendors to provide these statistics in the dashboard or build them into SIEM or other reporting tools.
Threat intelligence and event data are also useful to security operations and incident responders. API-based integration with Syslog SIEM and other SOC solutions is often lacking. Large security vendors with broader portfolios of security tools (e.g., Symantec, Cisco, Sophos, Trend Micro, and Microsoft) are increasingly promoting the integration benefits of multiple security tools into a single incident response console. SRM leaders will have to weigh the operational benefits of an integrated and automatable platform product against the effectiveness of best-of-breed solutions.
Machine learning (ML) will play a greater role in new email filtering roles. Once sending patterns are stored for impostor detection, they can be mined to help solve more complex problems such as preventing emails sent in error and diverting activist email floods. Solution providers like Tessian are using ML trained on outbound email, along with data loss prevention (DLP) and policy rules, to detect when employees accidentally send email to the wrong recipient. ML-based on inbound email may also be capable of detecting inbound activist-type emails. Large organizations are often targeted with grassroots email campaigns that flood executive inboxes. Currently, filtering these campaigns into custom quarantines is a manual policy creation.
Recommendations
SRM leaders should:
- Upgrade to the latest version of the incumbent SEG that includes advanced phishing protection and asks the vendor for a configuration audit to ensure that all advanced phishing protections are enabled.
- Plan to migrate to cloud-delivered solutions at next contract renewal or particularly when migrating mailboxes to the cloud.
- Budget for advanced phishing protection with deployments of Office 365. Even Microsoft's solution comes at an added cost.
- Favor solution providers that are focused on the phishing problem and have a history of rapidly responding to new attack types.
- Consider BEC protection mandatory in phishing solutions, and favor providers that are attempting to use machine learning to identify sending pattern anomalies.
- Favor solutions with an adaptive security architecture that can detect and respond to threats that evade initial filters.
- Consider secondary layers of security such as endpoint protection, SWG, user and entity behavior analytics (UEBA), and MFA as part of an effective phishing protection solution.
- Favor solutions that do more to inform the security team about attacker motivation, targets and threat patterns juxtaposed with global or vertical industry patterns.
Integrate Employees Into the Solution and Build Capabilities to Detect and Respond to Suspect Attacks
Phishing education is an important part of a security education program (see "Critical Elements for Your Security Program's Success"). However, few phishing education programs are fully integrated into the email flow, and simulated phishing attacks lack the context of real-world attacks. Integration of phishing education into email flows — using real neutered phishing messages as education emails, for example — is much more accurate. Phishing education programs must also explain the specific protection provided by the SEG, how to interpret its effects on emails (i.e., long, decorated URLs are acceptable) and when it is safe to open or click links.
More problematic, however, is that few email security solutions actually offer any visual indicators of trustworthiness to help end users make better decisions in real time. It is unreasonable to expect employees to turn into experts at spotting rapidly changing phishing attacks and not give them any tools to help identify phishing emails and report them in real time. SEG solutions have a tremendous amount of contextual information about every email, but these solutions fail to pass on indicators that employees can use in evaluating the trust level they should put in specific emails. Indeed, even standards such as DMARC, DKIM, and SPF, which should increase the confidence level in an email, are hidden from end users. (Note that the forthcoming standard for brand indicators message identification [BIMI; see Brand Indicators] is really designed as more of an incentive for branded companies to publish DMARC; however, it will provide a limited visual clue for receivers.) SEG solutions have much more data that could be presented to users such as the reputation of the sender, previous communication patterns, internal or external mail server, and suspect content keywords. Emerging solutions (e.g., IRONSCALES, Gmail) are available that can provide valuable information to the end users to make better decisions, but the industry at large needs to do much better.
Even if users are well trained, they generally do not know what to do with a suspect phishing email. Should they just ignore it or report it? If they report it, will the security team actually know what to do?3 Is a process in place to identify phishing emails, and can it handle the volume if every user diligently submits suspected messages? (One Gartner client set up an email phishing reporting button in Outlook and it increased the number of suspected phishing messages submitted to the SOC by 800%.) Security operations centers need to automate4 the submission and resolution of phishing attacks, including searching for similar attacks across all inboxes.
User education is a good start, but it is incomplete if users are not given more contextual information about emails and a means to easily report suspected emails. And security operations centers must have adequate staff, tools, and automation to respond to submitted phishing messages.
Recommendations
SRM leaders should:
- Favor SEG solutions that are designed with "report phishing" email client plugins with associated automated workflow to evaluate submitted messages.
- Seek out solutions that can provide visual indicators of trustworthiness of emails. Explore existing SEG policy capability to add contextual information about emails such as "external" versus "internal" senders, DKIM/SPF/DKIM success and URL categorization.
- Ensure that continuous phishing education training and simulated attacks are in context with the current attack pattern and users understand the email security solution protections and limitations.
- Establish a clear process for submission of suspected phishing emails and educate users on how to use it.
- Prepare security operations teams for suspected phishing submissions, and develop an automated workflow to investigate suspected emails, communicate with submitting users and search other mailboxes for similar messages.
Work With Business Managers to Develop Standard Operating Procedures for Handling Sensitive Data and Financial Transactions
Impersonation attacks will continue to exploit casual and formal business transactions, data handling, and supply chain processes in an email. Technical controls for BEC-type attacks alone are insufficient.
Phishing attacks targeting credentials will continue to increase as applications and data migrate to better-protected cloud providers and identity federation and single sign-on (SSO) proliferate. Credential attacks enable attackers to take over email boxes. Attackers will often then exploit access to email systems to divert legitimate business transactions using legitimate email accounts. SWG filtering cannot stop these attacks. Moreover, impersonation attacks will not be limited to email. Already attackers combine email and voicemail. Expansion to other social channels for more sophisticated attacks is likely.
The bottom line for the business is that email is not a trusted source of identity. This means that business processes that use email are not properly authenticated or authorized. Business process owners must establish formal guidelines for ensuring that significant banking and data handling processes include a method to positively establish the identity of the requestor and their authorization for the transaction. SRM leaders should assist the business in finding alternative transaction channels outside of email for at-risk transactions. For example, HR cannot change direct deposit banking information without telephone confirmation initiated by HR. Moreover, banking and data managers should be educated on current phishing attack tricks and methods. Of course, the security concerns must take into consideration the risk and the cost of implementing out-of-band identity proofing.
Recommendations
SRM leaders should:
- Identify the business processes in the organization most likely to be targets of business compromise attackers.
- Educate business process owners and employees about the risk of BEC phishing attacks and the limitations of current solutions to address this risk.
- Help the business owners with technical solutions to institute standard operating procedures for verifying the identity and authority behind emailed instructions.
- Where necessary, assist the business in finding alternative transaction channels, outside of email, for at-risk transactions.
Evidence
1 In 2017, the IC3 received 15,690 BEC/EAC complaints with adjusted losses of over $675 million. "2017 Internet Crime Report," FBI Internet Crime Complaint Center. In 2016, the IC3 received 12,005 BEC/EAC complaints with losses of over $360 million. "2016 Internet Crime Report," FBI Internet Crime Complaint Center.
2 "We discovered that over 98% of malware making it to the sandbox array uses at least one evasive tactic and that 32% of malware samples making it to this stage where what we could classify as 'hyper-evasive,' layering on six or more detection evasion techniques." "Evasive Malware Now a Commodity," Security Week.
3 In the case of the John Podesta Gmail phishing attack, an inexperienced and overworked help desk person responded poorly and said: "This is a legitimate email." Charles Delavan, a Clinton campaign aide, replied to another of Mr. Podesta's aides, who had noticed the alert, saying: "John needs to change his password immediately." "Podesta emails." Wikipedia.
4 Limited example security incident phishing workflow template. "Security Incident Phishing Workflow Template," ServiceNow.
Note 1
Business Email Compromise (BEC) Attacks
BEC attacks are phishing emails that do not have a payload such as a URL or attachment. Instead, they use impersonation and knowledge of the company structure or common transactions to convince employees to wire money or data or to change bank account information for pending payments.
According to the FBI, "The BEC scam continues to grow and evolve, targeting small, medium, and large business and personal transactions. Between December 2016 and May 2018, there was a 136% increase in identified global exposed losses." And between October 2013 and May 2018, there were more than 78,000 reported global incidents involving $12.5 million USD in the actual and attempted loss. See "Business E-Mail Compromise the 12 Billion Dollar Scam," FBI Public Service Announcement.
Note 2
Cousin Domain
DMARC and other email certification methods only attest that the email is from the domain in the email. However, phishers can send email using other similar-sounding domains such as Gardner.com or GartnerSecurity.com, for example, instead of Gartner.com. Phishers can also combine multiple alphabets (i.e., Cyrillic and western to create look-alike domains in IDN homograph attacks). For example, the Greek, Latin and Cyrillic "О" are different Unicode characters, but they look the same in the display. Phishers can even register near-match cousin domains and publish DMARC or other standards, making DMARC less useful as an indicator of email company authenticity.

Peter Firstbrook - VP Analyst |

Neil Wynne - Principal Analyst |
© 2018 Gartner, Inc. and/or its affiliates. All rights reserved. Gartner is a registered trademark of Gartner, Inc. and its affiliates. This publication may not be reproduced or distributed in any form without Gartner's prior written permission. It consists of the opinions of Gartner's research organization, which should not be construed as statements of fact. While the information contained in this publication has been obtained from sources believed to be reliable, Gartner disclaims all warranties as to the accuracy, completeness or adequacy of such information. Although Gartner research may address legal and financial issues, Gartner does not provide legal or investment advice and its research should not be construed or used as such. Your access and use of this publication are governed by Gartner’s Usage Policy. Gartner prides itself on its reputation for independence and objectivity. Its research is produced independently by its research organization without input or influence from any third party. For further information, see "Guiding Principles on Independence and Objectivity."


You must be logged in to post a comment.