SECURE-IT | Total Control eMail security (TC)
Total Control (TC) subscribers experience the ultimate in automated intelligent control over messages received and sent.
Administrators and designated subscribers can tailor settings for designated users, organizations or entire communities - minimizing risk and redundancy.
All TC subscribers enjoy an exclusive range of power, flexibility and security not available elsewhere.
Key features
- Block spam, viruses and volume-based attacks from reaching your IT infrastructure
- Inbound queuing assures continuous service during unexpected interruptions to back-office and cloud messaging services
- Outbound filtering protects messaging reputation, entirely avoiding IP address blacklisting
- Address-on-the-Fly™ technology protects email address integrity by temporarily serving email addresses, discontinued later
How it works
- TC replaces common email security servers with a 100% reliable and privately managed security service
- Nothing changes in your networks - not servers, clients, agents, plug-ins or hardware-probes.
- Instead, TC filters every message and attachments through every step below.
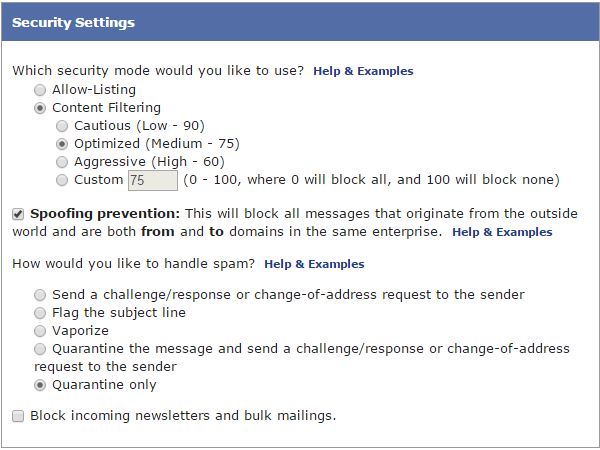
A wide range of capabilities and blended defense delivers maximum control.
Subscribers often favor one way to deal with unwanted content and senders. Some people like the precision of allow/block lists to authorize or block specific senders or domains (often called “whitelisting” and “blacklisting”); others prefer the simplicity of content filtering; still others like the added effectiveness of challenge-response methods.
Likewise, similar methods prevail for messages classified as spam. Some prefer a daily email summary of blocked email; others, to examine their spam quarantine folder directly; still others may choose to divert their daily quarantine summary to an assistant for checking. Some simply don’t want to be bothered with checking spam folders at all, electing to vaporize anything that appears a remotely offending.
TC has the versatility to accommodate all of these preferences, and more. Importantly, capabilities can be blended to provide more effective protection than can be achieved by using any one technique independently. In particular, customer experience shows that by combining content-independent techniques with content-based filtering techniques, TC yields dramatic improvements in user control over inbox access.
Address-on-the-Fly™ protects the user’s primary address.
Address-on-the-Fly™ (AOTF) provides users with a unique, liberating capability for disclosing email aliases as alternatives to their primary address. Its simple implementation does not require any user interaction with the service, and it spares the use of one’s primary address from public or uncontrolled disclosures that may result in new sources of spam. All AOTFs automatically resolve to the user’s single inbox.
This popular feature provides an effective means of controlling inbox access, blocking spam, making phishing attacks immediately evident, and preserving the long-term integrity of the user’s primary email address.
Savvy email users have long recognized the value of using multiple email addresses, and general awareness is growing. In fact, many consumers now employ multiple addresses, albeit by maintaining separate email accounts. AOTF brings the power of this technique to a single inbox in a fully automated fashion. Learn more here about Address-on-the-Fly
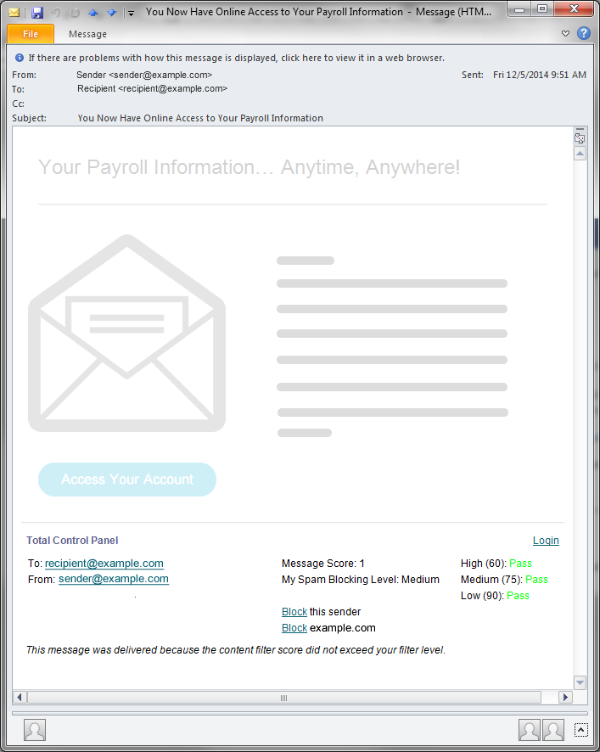
An in-message control panel informs and empowers the user.
The unique in-message control panel provides a simple and intuitive means for bi-directional communication between the user and the service, presenting the user with message-specific options for controlling inbox access.
The control panel reveals the envelope To: address in order to bring out information about the message. For example, a message recipient can see when one party has shared the recipient’s address with another party. Subscribers employ the control panel to communicate with the service, amending their access policies for specific senders and addresses.
Experience confirms that users find the control panel to be simple, helpful, and effective. It’s easy for users to understand, the choices are intuitive, and most of all, users like the ability to take concrete, immediate action to squash a spammer.
Some users also employ the control panel as a safe alternative to the unsubscribe function in many emails, which some people no longer trust out of fear that it merely confirms a valid address and alerts a spammer to a “live” recipient.
Control panels are available in English, Spanish, French, German, Brazilian Portuguese, Dutch, Italian and Chinese, with Russian and Hebrew on the way.
Outbound email auditing helps protect one’s brand and avoid email disruptions.
No legitimate correspondent or domain owner ever wants to be in the position of inadvertently sending out spam and viruses. It’s not only embarrassing, but can damage one’s reputation or brand. It can also lead to severe operational disruptions if one’s email server gets “blacklisted,” as this dreaded outcome prevents the delivery of all mail, good and bad, to all recipients at domains that utilize the specific blacklist to preemptively block senders deemed to be abusive or careless. This can be especially bad for Internet Service Providers (ISPs), as a blacklisted server affects all domains supported by that server, whether responsible for the outgoing spam or not.
TC outbound mail auditing addresses these serious concerns by inspecting outbound messages using pattern matching, statistical heuristics, and fingerprint filtering and scanning techniques. Every message passes through a series of checks to determine conformance with message size and volume limits, to identify message type (for example, to isolate bounce messages to avoid “blowback spam”), and to scan for spam and viruses.
Each outbound message is then routed according to its categorization. For example, policy-offending or suspicious mail is placed in a quarantine queue, while non-delivery receipts are routed through a server that is dedicated to such traffic. If that server becomes blacklisted, it won’t jeopardize one’s operations. Messages found to be spam or to contain viruses are also placed in the quarantine.
When a message fails a security or policy check, designated administrators are alerted to offending and/or suspicious content. These alerts specify the reason for placing the message in the quarantine; for instance, because the message content exceeded a size or “spamminess” threshold set by the originating domain, or it contained a virus, or the volume of mail from the specific sender exceeded a specified message-rate-over-time threshold.
These alerts can be tailored to comply with specific policies. With each alert, administrators can further tailor responses, such as releasing some messages, vaporizing other messages, dispatching multiple messages. In addition to alerts, TC provides bounce notifications, informing senders, for example, a limit on the size of email during a 30-day trial period.
TC provides the capability to implement rate limiting for individual users, blended with content and domain filtering, and controlled through point-and-click gestures. For example, if a user sends 20,000 messages in a specified time period, x% of which exceed a pre-set content-scoring threshold, TC will queue those message as suspicious followed by an alert to the email administrator for review. TC also profiles standard email usage patterns of individual users for further reporting and analysis, targeting suspicious senders or zombie PCs for remediation.
Discover more Total Control features
“Address-on-the-Fly” is a registered trademark of Sophos Limited or one of its affiliates. All other product and company names mentioned are trademarks or registered trademarks of their respective owners.